One of my clients needed a site-to-site VPN. Searching online I found some sites that were very helpful. I decided to configure it using tun rather than tap. The difference between tun and tap is tun can tunnel traffic between 2 different subnets where tap you have to use the same subnet on both ends (they call this bridge). Both ends have different subnets and I did not want to change them. The other reason is tap is slower because it sends more traffic over the VPN then tun.
Now the first site describes on how to setup the initial OpenVPN configuration. Following the instructions on this site of Part 1 and Part 2 got me the initial connection. If this is the first time setting up an OpenVPN on a Tomato router I suggest that you DON’T check the box Start with WAN in case you make a mistake. I did in the certificate and it made the router none functional. Because I specified start with WAN even a reboot failed to work. I had to reset my router. Start with out start with WAN. Once the initial connection works then you can go back in to Tomato and check the Start with WAN. The instructions setup using tap so if you want to make a tun connection then only follow the certificate part (Part 1 and Part 2 for inserting Certs into Routers) where you download the OpenVPN, install and make the certificates. One thing it did not specify is when you run the setup for installing the OpenVPN make sure you check all the boxes. Make sure you check the OpenVPN RSA Certificate Management Scripts or you won’t be able to run the scripts in Part 1. When it says the Common Name make sure you write it down. You will need this later. So if you follow the instructions correctly in creating the certificates and you put them in the server and client Tomato routers.
After the certificates Keys are entered into the Router then here is the instructions for tun to work so that you can ping both client to server AND server to client.
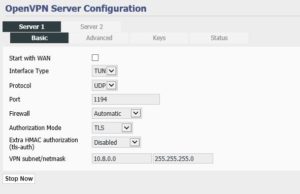
On the Server Router here is my configuration:
BASIC
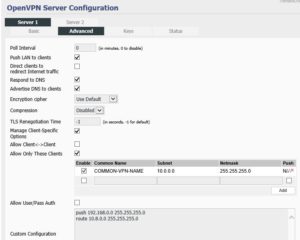
Now the Advanced
For my example this is my configuration:
Server subnet 192.168.0.0
Client subnet 10.0.0.0
Common Name used in the certificate creation COMMON-VPN-NAME
How this works is the push and route commands in the Custom Configuration allows the client side to ping or connect to the server side.
For the server side to ping or connect to the client side you have to specify Manage Client-Specific Options. Allow Only These Clients checked and then add the client Subnet. You have to specify Enable and you have to specify Push. Make sure the Common Name is the same as the Common Name used in creating the Certs/Keys or it won’t work.You then need to restart the VPN (Stop Now and then Start Now) on both Server and Client.
One thing I found out in another forum is when I configured the Client part to allow Ping connection from the Server to the Client side I could only ping the client router (10.0.0.X) I could not ping the Windows PCs. If you want to ping you have to disable the firewall on the Windows PC. Connection will work fine with the firewall enabled it just won’t respond to pings outside the Windows PC’s normal subnet.
This is the forum that got the client to server ping working
This is the forum that got the server to client ping working


Recent Comments